There’s good news and bad news when it comes to cybersecurity. The good news is that Nominum, a global player in the ISP-grade recursive server market, has released their semi-annual report on the state of cybersecurity. The bad news is that, umm, the hackers are doing pretty well.
There’s good news and bad news when it comes to cybersecurity. The good news is that Nominum, a global player in the ISP-grade recursive server market, has released their semi-annual report on the state of cybersecurity. The bad news is that, umm, the hackers are doing pretty well.
As a CIRA partner, we look forward Nominum’s regular security reports, and once again they don’t disappoint. However, what is disappointing is that from March to August 2017, Nominum tracked a seven-fold increase in malicious queries. Ouch.
Nominum is uniquely positioned to offer up this kind of analysis. In addition to offering DNS resolving capability, they have built impressive capabilities in security data science. Because of their global presence they have visibility into 1.7 trillion DNS queries per day and use this information to find new threats that distribute phishing content, ransomware, botnets, and other malware. It is a unique and very effective way to look at the threat data and they are able to add over 100,000 new threats to the block list daily. This technology is behind the D-Zone DNS Firewall service from CIRA that is installed in servers peered to Canadian IXPs.
The report does offer some hope. While cybersecurity threats continue to escalate, the industry is getting better at recognizing the threats and responding in kind. The global cost to productivity is enormous – but organizations are starting to be more aware and to take more action.
A few highlights from the report:
- DDoS attacks are getting larger and they are not just being used for network destruction anymore. Extracting ransom and influencing elections are now common motives for DDoS attacks.
- In one example, Nominum observed a domain that received 89 million queries in a ten-minute window (compared to the #2 ranked Google.com receiving 300,000). The impact was a drop in legitimate DNS resolution by 20%
- Pseudo Random Sub Domain (PRSD) attacks continue to persist. On one day in March, 55% of total subdomains on the web were created by malicious actors.
- Soapbox is a family of Trojans that allow remote attackers to take control of infected devices. Nominum observed 500-1000 clients infected per hour (based on a callout to command and control servers) showing the scope of devices already infected.
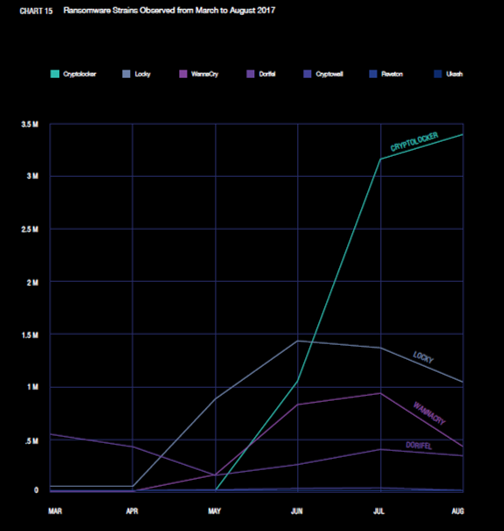
- Queries from Locky and Wannacry trended down from their peaks in early summer but Nominum saw a huge explosion in Cryptolocker as it emerged redesigned and more deadly from a period of dormancy. A great demonstration that treating the infection is only a temporary solution before it comes back.
You can get the report here.
Rob brings over 20 years of experience in the technology industry writing, presenting and blogging on subjects as varied as software development tools, silicon reverse engineering, cyber-security and the DNS. An avid product marketer who takes the time to speak to IT professionals with the information and details they need for their jobs.





