As an employee, security sometimes feels like a barrier to me doing my job, and it can be just downright annoying. But a few months back, I became part of the solution.
CIRA manages the .CA registry. Part of that means keeping the DNS functioning for the country-code top-level domain, ensuring all second-level domains can continue to work. If we can’t function as the authority for .CA, then the DNS can’t function as an authority for a lot of domains.
We have a lot of responsibility, which means we take cybersecurity seriously.
As an employee, security sometimes feels like a barrier to me doing my job, and it can be just downright annoying. I have to juggle constant system updates, blocked applications and websites, complicated password policies, endpoint firewalls, and DNS-based rules. All of these technology measures can make me feel like I am a risk to be managed.
But a few months back, I became part of the solution.
Cybersecurity Awareness Training
CIRA now publically offers cybersecurity awareness training and phishing simulation as a service—and not only are we the service provider, we are also a client.
This training platform is a one-stop-shop that combines traditional courses, awareness and perception surveys, phishing simulations and company-wide measurement. This is a significant step-up for the days of yore when IT cybersecurity training meant a 45-minute pizza lunch in the cafeteria with a sign-up sheet that proved you attended.
Most importantly is the integration of our training with phishing tests. These days, most organizations do some form of phishing tests or simulations, but the ones I’ve experienced have never felt effective. Everyone in my department would get the same test at the same time, and we’d never receive any feedback or results reporting on the tests or our improvement. As a user, I still felt like a managed risk and even resented being tested.
On the flip side, our IT departments felt these tests took too long to administer and report on. Being able to prove the effectiveness of our security programs with data was a long and tedious process.
Our training tool sends out unique phishing tests randomly to everyone at CIRA so nobody can be the “gopher” and alert others that a test is coming. And if you do end up falling for a phishing test, you immediately get recommended appropriate training that is customized to that test. I might be good at recognizing social media email scams, but if I fell for a storage application scam (like a fake Dropbox login), I’d get more storage-related training. To me, the training feels highly relevant.
Using our Cybersecurity Awareness Training, my perception of our training and testing has completely changed. With this product, our goal is to “transform users into a human firewall”. While this sounds a bit intense, there’s a reason it’s a term that’s highly used in the cybersecurity industry—employees are a primary, direct target for attacks, and their awareness and diligence are incredibly valuable as part of every organization’s cybersecurity solutions.
As a user, what does it mean to me about being part of the solution?
- I’m being assigned courseware that isn’t intrusive, and when completed counts towards my risk score.
- I receive completely random phishing tests that nobody else is getting, so I’m encouraged to report bad emails to IT. When I report, they get counted towards my risk score and I get thanked for my diligence – not shamed.
- I can take additional cybersecurity courses to improve my risk score.
- I actually get to see my risk score, and how my training is helping me improve. Best of all, my risk score is compared to the rest of CIRA, and I’m winning!
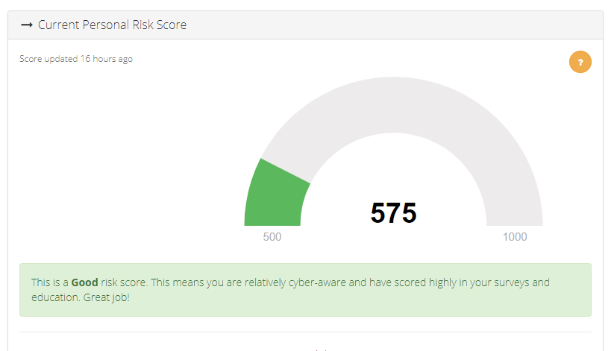
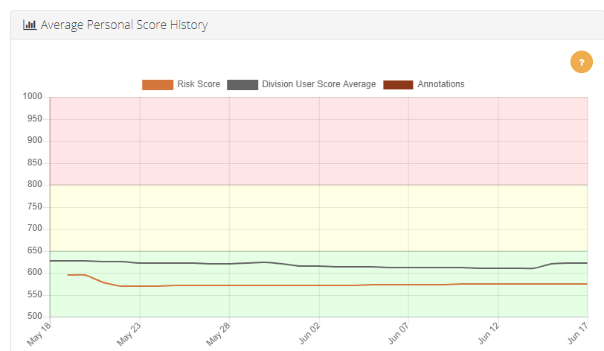
Fully transparent personal cyber risk score
One of the biggest gaps I’ve felt with other security training tools is that I’d have no idea what my performance was, and whether my training even mattered. You can see from the screenshots above (taken from my personal dashboard), that my risk score is 575. This score is a combination of my department, my role, my access to systems, and my success with training. When compared to the rest of my team…I’m winning!
Phishing simulations help users build a good habit
This level of engagement has encouraged me to report real (and not just simulated) phishing attempts. I’ll admit, this isn’t something I really did before. I didn’t see a point when my inbox was filled with spam, sales emails, newsletters, AND malicious content. Because there was so much content, I just ignored it altogether. This might seem good from a corporate risk perspective since I’m not easy to phish, but the real problem is that I wasn’t part of the solution by helping others at CIRA.
Our IT team tells me that the vast majority of malicious email gets caught in our other layers of security, but every once in a while one gets through because it’s a spear phishing campaign uniquely designed for us at CIRA, or a legitimate email points to a site that used to be safe and was only recently hacked.
The point is, the importance of actually paying attention and reporting bad links and emails was lost on me. Since our own DNS Firewall data tells us that users that click on bad links tend to do so within a few short hours, this makes quickly catching and blocking them a very high priority. So now I actively report emails, making me a part of the solution.
We talk a lot about adding multiple, unique layers of defence that protect each other. Effectively trained and vigilant people are a vital part of that defence in depth. Across users in other organizations, we’ve found that people using effective Cybersecurity Awareness Training are more likely to report malicious emails, and have a 3x reduction in clicking on malicious links.
Has our new training worked on me? By virtue of my job I am pretty cyber-aware, but I can say that I have improved and am now enjoying some internal competitions with others on my team to see who is winning at lowering our risk score!
Rob a acquis plus de 20 ans d’expérience de la rédaction, de la présentation et du blogage à l’intention de l’industrie des technologies. Il aborde des thèmes aussi variés que les outils de développement de logiciels, l’ingénierie inverse de Silicon, la cybersécurité et le DNS. De fait, Rob est un spécialiste du marketing passionné qui s’adresse aux professionnelles et aux professionnels des TI en leur donnant les renseignements et les précisions dont ils ont besoin pour s’acquitter de leurs tâches.





