What do Canadians love to do (second) most on the Internet? It may surprise you that the answer is banking. Is the DNS of the financial sector protected?
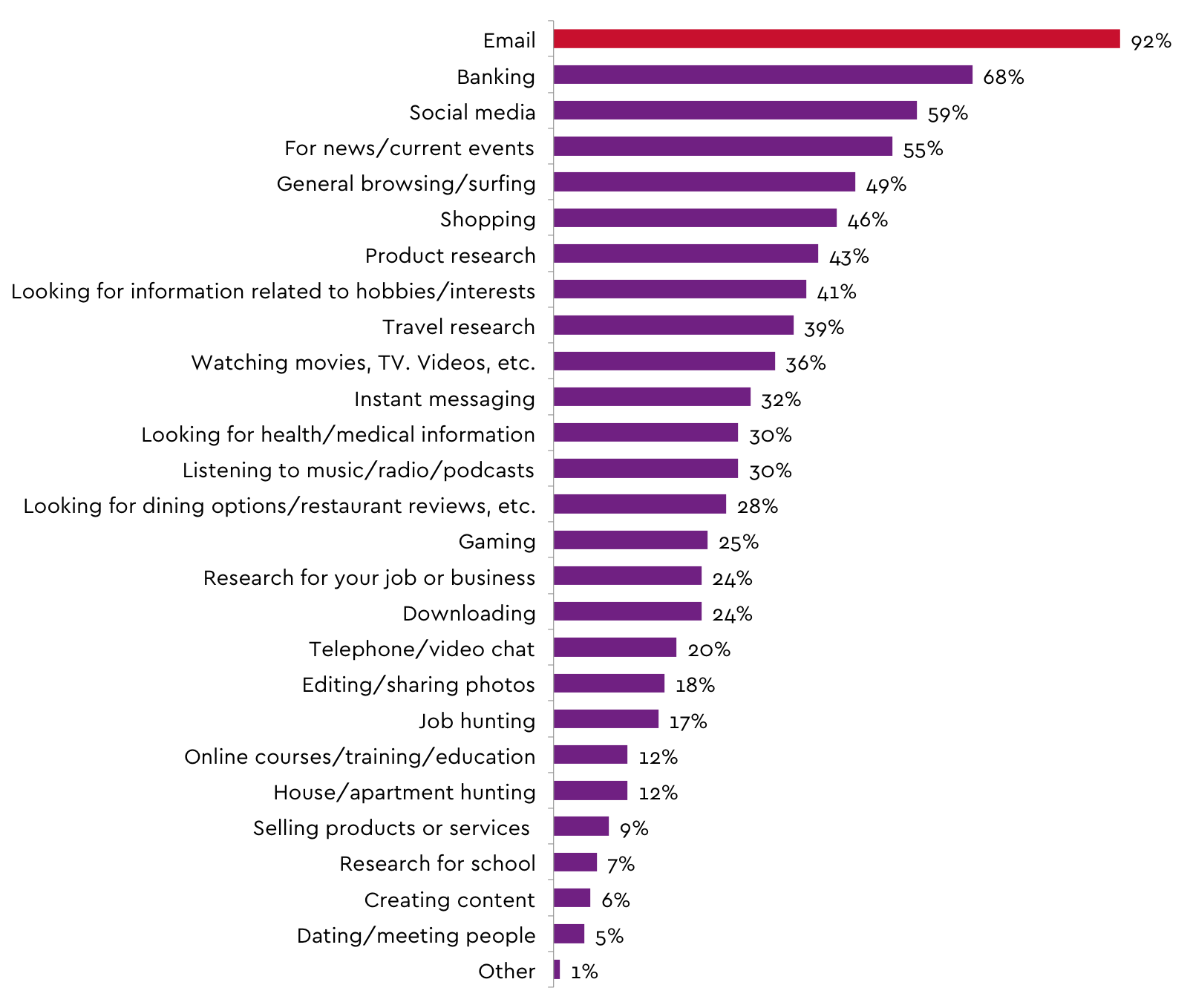
What do Canadians love to do (second) most on the Internet? It may surprise you that the answer is banking. In a survey commissioned by the Canadian Internet Registration Authority (i.e. “us”) Canadians were asked what activities they did online on a regular basis and banking came second with 68% of people responding in the positive, second only to the far-and-away leader, email.
What Canadians are doing online, CIRA Internet Tracking Research, 2016 Factbook
It seems we love our money almost as much as we love emailing loved ones funny pet memes. In fact, banking out-ranked “general browsing” or surfing. It also out ranked other useful activities like job hunting, school research, training, content creation and work-related research combined.
The big banks, small, banks, online-only banks, credit unions, insurance companies, Real Estate Investment Trusts (REITs) and more, have made big business out of online banking both to end users and between each other. For Canadians this has been a huge benefit as we don’t need to wait in line, application forms are trivial to complete, and emailing money is as easy and fast as the click of a button. For financial institutions this has helped to deliver operational efficiency gains and reduce costs.
Given the central role that banking websites have for Canadians we thought we would take a look at the authoritative DNS for 150 financial institutions in Canada. This look involved a simple WHOIS review of their DNS records to see how it was being managed to see how resilient it is to cyber-attack. A future blog will delve deeper into a full DNS analysis on a subset of these organizations to see how well it is configured and how widely deployed Anycast environments are. However, anyone interested in a review of their DNS now can contact us today using our signup form.
Respond to the increase in DDoS attacks by including a backup DNS supplier in the IT architecture
This week news broke of banks in the UK being hit with DDoS attacks, including Lloyds bank experiencing some customer-impacting outages. While specifics aren’t being disclosed, in the latter instance the impact suggests an attack on the application layer. However, in today’s world, multi-vector attacks are becoming common and so networking infrastructure also needs to be protected. Since our ballywag is the DNS, that is what we will talk about.
A best practice for banking applications is to have at least two authoritative DNS providers. The DNS translates the human-readable website address into the machine readable IP address. Without it, nothing online works because it can’t be found. In the ideal scenario, one DNS network would be close to their customer base (i.e. Canadian) and at least one DNS network is an anycast solution. For a financial institution that has diversified to international markets, we would even make the case for an in-region authoritative DNS for every operating unit.
In an anycast scenario you have a network of DNS servers around the world and layer 3 routing sends queries to the geographically closest server. As a result the response time is faster for local users and when DDoS attacks originate off-shore they get soaked up where they occur. This leaves local traffic functioning. For Canadian traffic there is only one organization that has a Canada-first global network — CIRA.
With all the recent headlines it should come as no surprise that the Akami state of security report published Q3 2016 stated there has been a 71 per cent increase in DDoS attacks year-over-year. Attacks are growing ever larger – and the DNS is a popular target in single and multi-vector attacks – attacks that are mostly originated offshore. The growth in IoT devices has served to compound the issue as demonstrated by the over 1Tb sustained attack against Dyn (a major global DNS service) last year. In fact, according to the Arbor networks infrastructure security report, DNS operators are being targeted at a rate of 8,000 per week (a DNS operator is basically anyone running a nameserver).
In light of this we took a simple look at the some of the bigger banks name servers and found that Verisign and Akami were the two most common providers. This was not a big surprise, but importantly, we only saw direct evidence (based on nameserver listed) that one, Desjardins, had taken the step of having a second DNS provider. This is a fairly simple analysis based only on the hostname, but based on the providers we found it is likely reasonable. In a geo-located content delivery network (CDN) scenario, making the decision to have a backup DNS provider needs some architectural thought, but in other scenarios it is a necessity in 2017. In addition to the big brands, we took a look at complete cross section of financial services in Canada, including some credit unions, life insurance companies, investment companies, pension plans, real estate trusts and more to find virtually no evidence of instances of dual-supplier environments.
This puts them at risk of outage and Canadian at-risk of losing their second favourite reason to use the Internet.
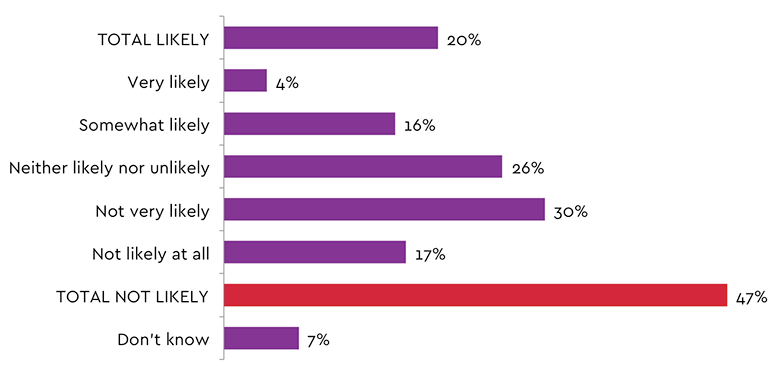
What can it mean to your bottom line if you are successfully attacked? Going back to the survey mentioned in the beginning of this blog, we asked Canadians how likely they were to make a purchase from an organization following a cyber-attack and a full 47% percent responded “not likely”. The average Canadian may not also recognize the difference between a nuisance attack and a data breach.
Likelihood to buy from a company following a cyber-attack
Given the low cost of adding a second DNS provider against lost revenue from even one lost mortgage builds a strong case for it.
Rob brings over 20 years of experience in the technology industry writing, presenting and blogging on subjects as varied as software development tools, silicon reverse engineering, cyber-security and the DNS. An avid product marketer who takes the time to speak to IT professionals with the information and details they need for their jobs.





