How do phishing simulations work?
Phishing simulations are written and designed to look like real phishing emails.
When a user receives a suspicious email, they should forward it to [email protected].
If the email was a simulation from the training platform, they will get an auto-reply email immediately, saying congratulations, you “caught a phish” and their risk score will improve. If a user clicks on the link in the phishing simulation, they will be assigned a remedial course.
If it was not a simulation, they will get an email providing guidance on what to do next.
What will the initial training look like?
Users will:
- Complete a survey: Users will answer questions on their cybersecurity behaviours and perceptions (e.g. “Have you shared your work password with someone else?”).
- Take four courses: Users will learn cybersecurity basics and take a short quiz at the end of each course.
- Get sent three simulated phishing emails: Three phishing simulation emails will be sent to them, and the user can forward them to a phish forward address.
These activities determine a baseline risk score for each user, which will go up and down over time, based on their interactions with automated monthly phishing tests.
The admin can view the risk score for each user and the average score for their entire organization, and access reports which provide guidance on how to reduce cyber risk.
What ongoing training will users receive?
To keep cybersecurity top-of-mind, users will be assigned a course every two months. A few days after a user completes the course, they will receive a phishing email that relates to the course material.
Monthly phishing
Users will also receive an automated phishing test (randomly selected from a bank) once per month. If a user “passes” a phishing test by reporting it, they will receive progressively more difficult phishing tests. If a user clicks on a link in a phishing test, they will automatically be assigned a remedial training course, giving them the opportunity to improve their risk score.
Admins can assign more courses at any time
There are over 100 courses available in the library (to view, go to Education > Courses) – if you see a course that covers a cybersecurity topic applicable to your workplace, click on Actions > Assign. Users can also self-enroll.
As an admin, what data can you view?
When you log into the platform as an admin, the dashboard shows data from the past 30 days.
Here are some reports we recommend admins check out to analyze training progress and identify cyber risks:
- Awareness and Education Report: Displays information about the current education status of your organization. Additionally, you’ll see information about the average time to complete training, average scoring.
- Course Summary Report: Displays all courses assigned/taken by that user in the division.
- Onboarding Summary Report: Provides a summary of where your users are in their education process.
- Security Dissonance Report: Displays the alignment of perceptions across multiple layers of your organization. On the area chart, you’ll see the perception overlap between senior management, IT security, and the on-the-ground reality in four key areas: Governance, Awareness, Technology, and Culture.
- Phishing Simulation Report: An in-depth analysis of the phishing simulations being sent out to your users. The report highlights the click rate, report rate, and specific statistics by division and phishing template.
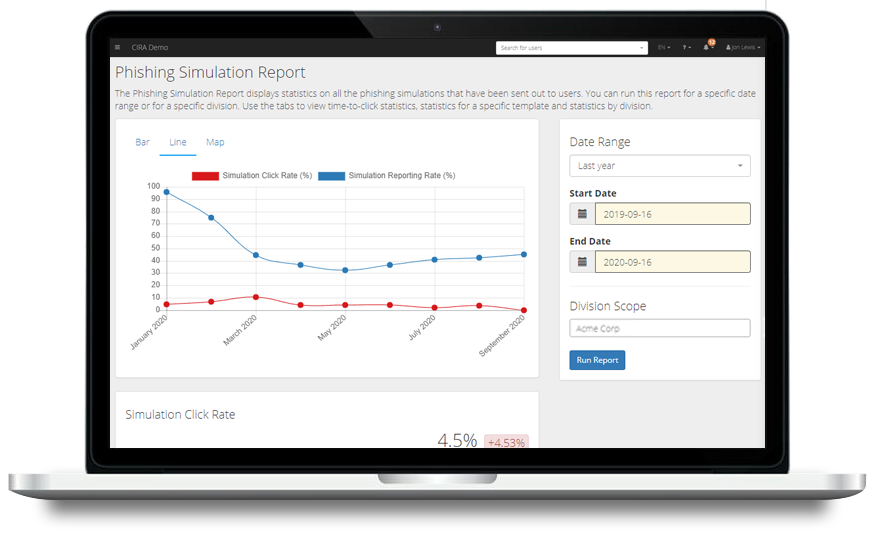
How can I analyze platform data and keep users engaged?
Our guide for implementing training describes how to analyze platform data and provides some ideas to keep users engaged in training to keep cybersecurity top of mind.